If you have Azure AD Premium P2 licences one of the reasons would of been to use Privileged Identity Management (PIM) as its a great tool to help provide "just-in-time" privileged access for resources where you don't need permanent access to.
In this article I will be going through how to onboard Azure resources into PIM so that you can control privileged access for your Azure resources as well. This means you can create conditional access policies for certain resources, resource groups, subscriptions or even management groups to ensure users only have the required permissions at the right time.
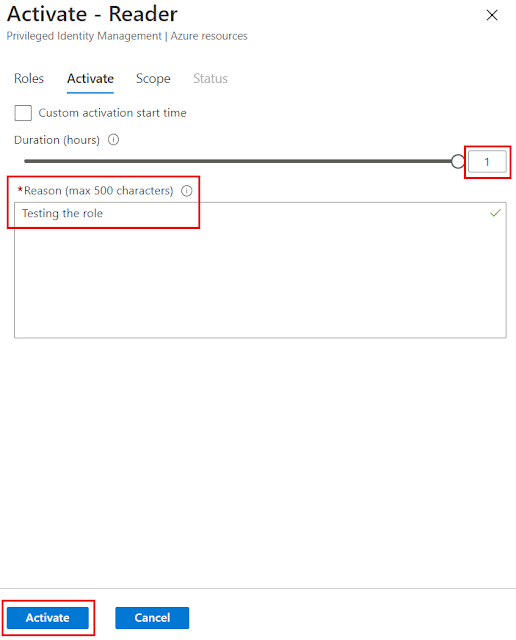
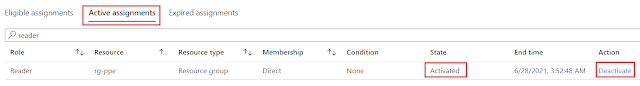
An example would be, by default you assign reader role for IT operations staff so that they can see all the resources. If they decided they need to make a change they would need to use PIM to activate a particular role you have assigned them which gives them permissions to make the change. As part of activating the role you might want to add some conditions. You might add that users need to use mutli-factor authentication, include a ticket number, require approval and limited the maximum amount of time the role can be activated for.
Below are the steps to get started to the journey...
There are some pre-requisites to start with
- Azure AD Premium P2 license
- You will need “Owner” or “User Access Administrator” role on the Azure resources that you wish to on-board to PIM.
Please note, once you have on boarded a management group or subscription to be managed you can not unmanage it. This is to prevent another resource administrator from removing Privileged Identity Management settings. The only way you can unmanage it is to delete the management group or subscription.
- Login into https://portal.azure.com.
Use the search bar to find "Azure AD Privileged Identity Management"
- Under "Privileged Identity Management" blade click "Azure Resources"
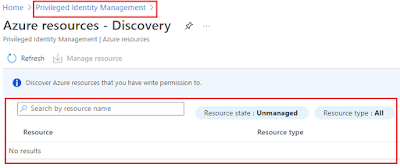
On this screen if you or someone has already onboarded some Azure resources you will be able to see it here. Please remember - You may not see some resource either if you don’t have the correct permissions for those Azure resources. Click on "Resource type" or “Directory” filter to provide you more options to see what resources have been onboarded. You may need to click on “Refresh” to ensure the content is refreshed as there has been a few times where the screen doesn’t seem to automatically refresh If the resource has not been onboarded yet, then click on “Discover resources” By default, this screen shows resource state “Unmanaged” and resource type of “Subscription”. As you can onboard subscriptions or management group you will need to change the filter so that you can see all the management group or subscriptions that have not been onboarded. Again remember to select “refresh” so that the resource screen refreshes. The screen below has been selected to show “All” resource type We are going select the resource we would like to onboard. For this demo we are selecting our “Free Trial” subscription. Once you have selected the resource/s that are to be managed by PIM you will be able to click “Manage resource” A warning message will appear highlighting that all child objects of the resource will be managed by PIM. For example, for a management group the possible child objects would be management group, subscription, resource group and resource. For a subscription the possible child objects would be resource group and resource. Click “OK” to continue On the top right of the screen if you click on the “bell” icon you should see the task of resource being onboarding Once the task has been completed you will see on the screen that the “unmanaged” resource is not listed there anymore. You will need to click on “Privileged Identity Management” to go back to Azure resources screen On the screen below you can see “Free Trial” subscription has successfully onboarded to PIM for you to start configuring roles to be controlled by PIM
We have now onboarded our "free trial" subscription to our Privileged Identity Management services which means we can start configuring just-in-time privileged access to Azure resources. In my next article I will describe how configure access to specific resources.