So you have gone through the hard work of defining tags and its value for all the resources in Azure portal which you want to make use of them when reporting the costing in PowerBi. Here I will describe how you can expose those tags for billing purposes so that you can filter your costing via tags as well.
First of all we need to get the API access key and enrollment number which you will need to ask whoever that has access to your Enterprise agreement information. You can check if you have access by going to https://ea.azure.com in case someone has given you access. Within the EA portal you will see your enrollment number on the top left of the screen which you will need to note down. To get the API access key you will need to click on "reports" then go to "Download Usage > API Access Key". You will see two keys, make sure you have a look at the effective date (remember US date format). Once you have decided which key to use then click on "expand key" and select "copy" to capture the whole key. If both has expired then clic on "regenerate" for one of them.
Now that you have both the enrollment number and API access key then we can move on to working within PowerBi desktop version. The version I will be using is dated as October 2020 (2.86.902.0 64 bit)
When you start up PowerBi desktop if you get the start up screen then select get data otherwise on the menu bar select "Get Data > More"
This should open up a new window and select "Online Services" followed by "Microsoft Azure Consumption Insights (Beta)" then select "Connect"
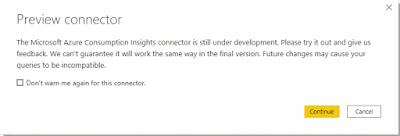
You will receive a warning about the connector is still under development but I think I have read somewhere below that they are not actually going to develop this anymore. You can click continue to carry on.
You will need to enter your enrollerment number which you have gathered at the start of this task. Once you have entered your enrollment number click "OK"
You will now need the Account Key which is actually the API key that you have gathered as the first step so enter the API key and select "Connect"
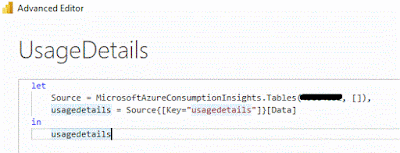
To keep it simple I will just select the "UsageDetails" table and click "Load". Now wait for the data to be downloaded which could take some time.
Once loaded you will see on the righthand side there is a "fields" section and if you scroll down you will only see "tags" as the possible selected field. The idea is to try and break out all the tags in this field so that we can can make use of the tags that we have defined and to use those as filters.
On the menu bar select "Transform data > Transform data"
You will be in the power query editor now. Scroll across to find the "Tags" column. You should see all your tag name and values all within this field. Right click on the column to bring up the menu select Transform > JSON. Give it some time to process
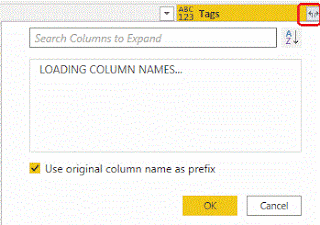
Once the transformation is completed click on the icon next to the Tags column as shown below and wait for the tags names to load up.
Select the columns you want and then click "OK". Again wait for the new columns to be created
Once they are created you will see them and they will be prefixed with "tags." followed by your tag names
At the menu of the Power Query Editor select "Close & Apply which would start to apply the query changes.
If you now look at the fields section you will see that the Tags field has disappeared and the tags values that I decided to expand are shown here for me to select.
So now you can build queries and make use of the tag values that you have defined for your resources in your subscriptions.