You may need to give it a bit of time by clicking around other parts of the subscription or sections of the subscription blade. Afterwards if you go back to the subscription properties you should see that the "Service Administrator" should have changed to the account you have specified. You can also go to "Access control (IAM)" then "Classic administrators" tab and that should of changed to the new account you specified.
Remember once you have changed it the "Account administrator" will lose access to the Azure Portal which is the affect that I was after.
Now the tricky bit is that we wish to change the "Service administrator" now as the user ([email protected]) will be leaving the organisation so how do we do this? Well you need to check again at subscriptions > Properties and see who is the "Account administrator". Next check if they have "owner" permissions or "Co-Administrator" role within the Azure portal by either logging in as them or go to the subscription "Access control (IAM)". You have 3 options to check the permissions.
"Check access" tab, if you want to check against the account you are logged in as then click "view my access" otherwise find the user account you would like to check then once you have located it then click on the name. You will have a new pop up blade which will display the permissions
You can see from the above image that "Kin Yung" account has the relevant permissions (Owner or Co-Administrator).The other two options are "Role Assignment" where you must see if the account is listed with "owner" permission. Under "Classic administrators" you will be looking to see that it is listed as "co-administrator"
If the account doesn't have permissions then they need to ask someone to temporary assign them the either the role of "owner" or "co-administrator". You can do this by going to the subscription > "Access control (IAM)" then "Add". Select either "Add role assignment" or "Add co-administrator"
If you select "Add role assignment" then make sure the role as "owner" and then search for the user account in your directory to be assigned the role.
Please Note: According to Microsoft documentation Contributor only "Grants full access to manage all resources, but does not allow you to assign roles in Azure RBAC" so you will need to grant the user "owner" permissions.
If the user logged in doesn't have permissions, you will see the "Service admin" button greyed so you need to make sure that the account has permissions by doing one of the options above.
Once you have granted the "Account Administrator" permissions to Azure portal then they can log in and change the "Service Administrator" to the desired account following the steps above.
Remember once you have finished this work to remove the account from "owner" or "co-administrator" permissions from the Azure portal.
Although Microsoft states that "Service Administrator" account is for classic Azure but I feel it's best to use an account that is valid in case there is something that needs to use it.
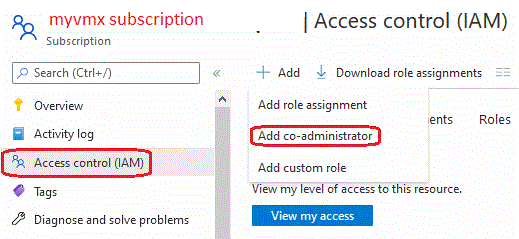
You can assign additional "co-administrator" by going to the subscription and selecting
"Access control (IAM)". Click on "Add co-administrator"
Now select the accounts that you wish to add as co-administrators from your directory and click "OK"
Once added go to the "Classic Administrator" tab and you should see the new account you have added and it will be listed as "Co-Administrator"











No comments:
Post a Comment